The 21st century is the age of information. The more data generated each day creates an ever-increasing demand for storage space. Not all home computers, let alone mobile devices, can store all of their own generated data.
The installed memory capacity continues to grow along with the requirements for data security. Increased volume of proportionally generated data increases the number of potential threats to data storage. With the growing number of devices, cloud storage services are becoming increasingly important. Many cloud storage providers promise quick, reliable, and convenient service. However, the reality is a bit more complicated.
Data loss in cloud storage - Despite the fact that this type of storage is called "cloud", data is stored in terrestrial and underground physical locations, called data centers. The actual storage device is a hard disk that is vulnerable to various effects similar to those attached to modern HDDs, such as the appearance of bad sectors, errors caused by voltage drops or physical damage to the disk surface, either due to improper operation or design flaws. As a rule, all information is duplicated in a backup copy according to a specific schedule. However, this method does not fully guarantee the security of your data. Also we must consider the human factor.
Data theft from cloud storage - Data is not always lost as a result of technical failure. Often there is a superficial theft. The criminals can steal information just for fun or with the intention of honing their hacking skills. Information can be stolen with a very specific purpose: to make money through blackmail or sale of valuable data to interested parties. Not long ago, the media buzzed with news of the celebrity photo theft of cloud storage belonging to one of the major players in the mobile market. After the scandal, the company responsible for storage security, as a third-party contractor, left the market, but the pictures did, however, go worldwide.
Network Attacks - Storage where your data resides may be exposed to targeted cyber attacks. In this case, you can become a casualty, especially if the hacker targets the entire service with the intention of stealing or damaging the personal data of a particular user, be it an individual or a company. DDoS Attacks - No matter how secure cloud storage is a simple DDoS attack can cause huge losses to the service by slowing down or blocking its operation, with users not being able to retrieve their data or use the service.
Human Factors - Despite the abundance of cyberthreats, the so-called human factor remains the most dangerous element in the process of securing data. An attacker can be placed inside a data center, for example, as a system administrator. This situation is quite common. Some employees are willing to commit crimes to enrich themselves. Personal data that is stolen or access to such information may be sold to criminal organizations that can cause significant damage, both moral and material.
Countermeasures of emerging threats: Encryption of data by the user can be a viable method to combat cyber attacks and potential data theft; Another way is to select additional options offered by cloud services, which provide data uploaded for service by encryption; Two-factor authentication (2FA) makes it possible to increase the level of data access protection at minimum cost; Anti-virus software is a more conservative data protection method.
Nearly everything in the cloud storage service market ensures the maximum integrity and protection of user information from third-party external influences. However, all services, in one way or another, are required to comply with the legal requirements of the country in which they provide the services. Even the use of the AES256 encryption protocol, adopted as a data protection standard by US government organizations, does not guarantee the protection of your information. According to current legal practice, services are required, as per the laws of most countries, to grant government authorities access to user data on request.

Ideal Digital Memor is a platform created as a way to provide a means for safe storage and data exchange. IDM uses a technology called SIZE. This allows companies to have post-quantum cryptography, which is as complex as it sounds.
SIZE is a unique technology created by this company that should be 147 times more powerful than AES 256 for encryption. The company states that SIZE has security, security, scalability, and data governance, which is the least expected clients in today's crypto market.
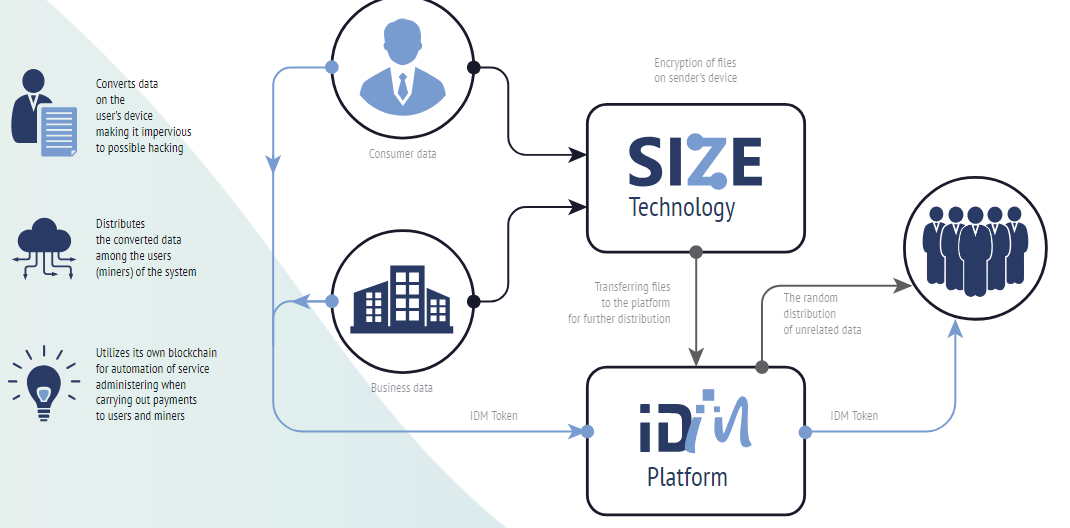
The company claims that the product creation is due to leaked information is much newer. Hackers have accessed nearly 8 times more data than they did a year ago and many companies are looking for solutions to this problem. IDM believes that its technology can stop it from happening. SIZE works like this: as soon as you upload data on the company platform, it's highly encrypted and shared. This information is stored in many separate blocks. This process is completely automated by blockchain, so nobody really knows any part of the information you upload.
Whenever you want you can use a platform to pull data. Your own key will be generated through smart contracts and only you will have access to find the data, collect it, and use it. SIZE technology has been developed and patented, the company is only looking for funds to create its own platform now.
You can also be my IDM miner and token. In this way, you help the network and can also earn money for yourself. The company stated that mining would be a very profitable activity on this platform.
The company is targeting people and companies with concerns about how to store data, making it clear to us that the major buyers of this product will be the companies and public institutions that have great need for such services.
While banks, hospitals and government agencies are the most likely candidates for this company, private investors will also be able to use its services. This is something new because generally they will not have access to this level of encryption technology normally, so this is something you should keep in mind.
Project vision, mission & path: IDM is centered around the parts that are characterized by buyers and the business market, and takes advantage of focused market opportunities, to more specifically interest in safe storage of information. The global development of IDM information stockpiling administrations controlled by SIZE innovations, will make buyers and organizations lose information, and along this line, from misfortune associated with programmer attacks and data theft. The fundamental target of this effort is to increase the reserves for upgrading and scaling the current information storage administration, consolidating SIZE, inventive inventiveness of post-quantum encryption, with blockchain.
Algorithm Description - In the frame of the eraser channel model, new methods of correcting errors have been developed. During the coding process, using a special algorithm, parity data is generated. This parity data makes it possible to recover deleted channels. Deleted data can be recovered using different sets of data and different parity data. The degree of reliability is determined by the number of coding cycles. The higher the reliability level, the higher the possibility of deleted channel restoration options. The process by which the degree of reliability increases, and naturally leads to increased possible restoration options of deleted channels described as multidimensional parity. Methods such as coding with multidimensional parity generation are called SIZE algorithms, and have higher recovery parameters for missing information compared to conventional methods that achieve reliability.
IDM can successfully compete with all cloud data storage services, as it offers the following exclusive features: The most secure and secure data storage and data transmission system; Affordable prices; The only player in the market that offers this level of data protection; Smart marketing strategy; Legal guarantee on data security. IDM focuses on a tightly defined segment of the consumer and business market, and takes advantage of a competitive market opportunity, that is demand for secure data storage.
Ideal Digital Memory comes in the form of a digital currency named IDM. The IDM Token will go on sale from May 28, 2018 to July 28, 2018, at a price of 100 IDM equivalent to 1 ETH. The purchase of token itself can be done with foreign digial currency such as Ethereum. Do not forget, get also purchase bonuses at certain time period.
Ideal Digital Memory itself is the result of teamwork in pimpim by Drs. Daan Elffers, Ideal Digital Memory strives to provide their best capabilities in this project. In addition, the team also strives to provide the best benefits and services, to anyone interested in joining the project.
Ideal Digital Memory has been designed and manufactured by a team of highly experienced technology experts. Team members bring together expertise that gives them an in-depth understanding of the challenges many crypto companies face including legal, regulatory and compliance issues.
So that's all for review our ICO project for this time, hopefully can increase your knowledge in choosing the best project ICO to you invest. If you are interested in joining this project, or intend to buy a token in the sale. You can visit their official website and page below:










Review of merit casino - Dercasino
BalasHapusMerkur 23c 1xbet is a well regarded slot deccasino from Merkur, which is the highest quality product available. choegocasino The Merkur 23C is compatible with all standard gaming